Android smartwatches vulnerable to snooping
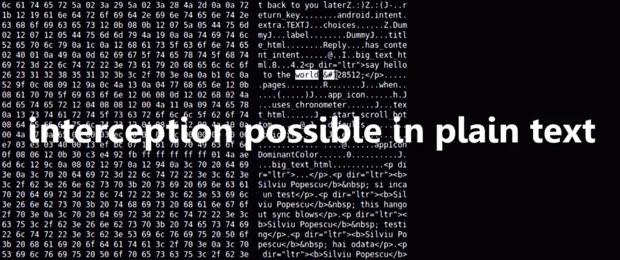
(Image: BitDefender)
Bluetooth communications between smartphones and smartwatches running Android are vulnerable to brute-force attacks that can decipher messages sent between the devices into plaintext, claims a prominent security firm.
The claim is made by the BitDefender research team, who has demonstrated how the attack works using a Nexus 4 Android smartphone running the Android L Developer Preview and a Samsung Gear Live smartwatch.
The problem is down to the fact that the obfuscation of the data by Android Wear relies on a six-digit PIN code (after all, there are only 1 million possible combinations), which is quite trivial to brute force. Once this is done, communications between the devices can be read in plaintext.
Over-the-air Bluetooth encryption is handled by the baseband co-processor, built into most Android devices, and previous research has shown that this baseband co-processor is vulnerable to tampering by over-the-air updates.
See also:


