Apple dismisses Masque flaw fears
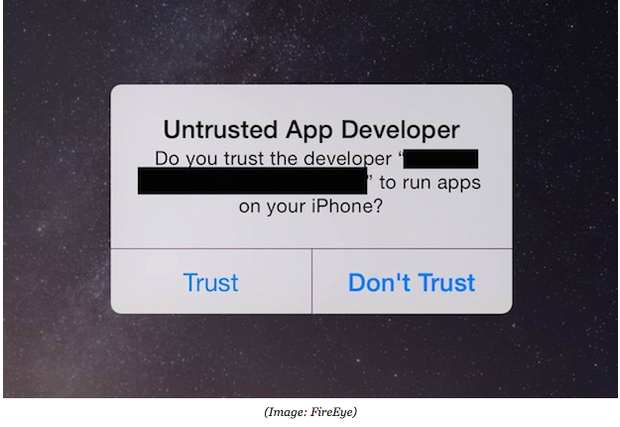
Apple has downplayed exploit fears stemming from the discovery of a security loophole that could trick users into downloading malicious apps onto their iOS devices.
On Monday, security researchers at FireEye detailed the discovery of the Masque bug in a new report. The researchers said the bug, in which apps running on iOS 7.1.1 and later — including the latest iOS 8 -- can be replaced with malicious, legitimate-looking applications. Once granted access to a user's device, these apps could theoretically install malware or steal user data.
The "Masque Attack" relies on users falling for phishing attacks and clicking on malicious links in either emails or text messages that point to an app download. It is important to note that these apps are outside the safer confines of Apple's App Store.
FireEye researchers said:
This vulnerability exists because iOS doesn't enforce matching certificates for apps with the same bundle identifier. An attacker can leverage this vulnerability both through wireless networks and USB.
Read this
Speaking to sister site CNET late Thursday, an Apple representative downplayed concerns, saying:
We designed OS X and iOS with built-in security safeguards to help protect customers and warn them before installing potentially malicious software.
We encourage customers to only download from trusted sources like the App Store and to pay attention to any warnings as they download apps. Enterprise users installing custom apps should install apps from their company's secure website.
In addition, the iPad and iPhone maker said that its operating system has built in protections to ward against malware downloads. Apple was not aware of any reports of customers actually falling victim to the attack, the representative added.
This is the second time in as many weeks that Apple has been scrutinized over the security of its products. Last week, security firm Palo Alto Networks discovered the WireLurker malware, which attacks iOS devices through USB connections. The malware was able to install third-party malicious apps, as well as infect Macs through the USB connection. Apple quickly issued a fix for the problem.
Read on: In the world of security

