Apple iOS Masque flaw dangers: Communication app infiltration discovered

Credit: CNET
The Masque security bug may pave the way for data to be stolen from legitimate app sources on iOS devices, according to Trend Micro researchers.
The Masque security flaw, which affects apps running on iOS 7.1.1 and later — including the latest iOS 8 — is based on a lack of enforced matching security certificates for apps with the same bundle identifier. In short, malicious apps can replace legitimate downloads by using the same bundle ID, and "intercept" user activity as a result.
Email or text-based phishing attacks are used to trick users into downloading legitimate-looking but malicious applications. While Apple is unaware of any reported incidents of the bug, researchers say the flaw could theoretically install malware or steal user data from iPads or iPhones.
Read this
Six clicks: Top free iOS, Android apps to learn how to program
No matter the age, learning a programming language is a marketable skill. Here are mobile apps to assist you.
However, most users need not worry as malicious apps are barred from the relative safety of Apple's App Store — so if you keep downloads within this sphere, the chance of your device being hijacked is minimal.
Apple downplayed concerns last week, saying that OS X and iOS have been designed with built-in security safeguards to help protect customers.
However, an additional facet of the Masque bug has been discovered. Trend Micro researchers have found a new way for malicious apps installed through a Masque attack to hurt a user: by accessing unencrypted data used by legitimate apps.
According to the security team, when Masque has found its way onto a device through enterprise provisioning — which allows companies to install homegrown apps on iOS devices without the need to be reviewed by Apple — data can be stolen from legitimate apps that lack encryption.
Trend Micro tested several apps and found that some popular iOS apps do not employ data encryption for their databases. The apps tested are message and communication systems, which means they store sensitive information including names and contact details.
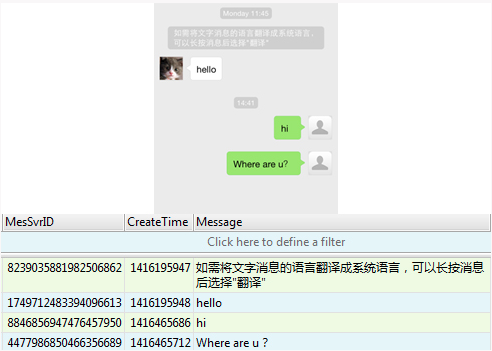
The image above shows that incoming and outgoing messages in a popular IM app are unencrypted, which means any malicious info-stealing software on a device can lift this data. The image below, showing a Chinese messaging client, had the same results.
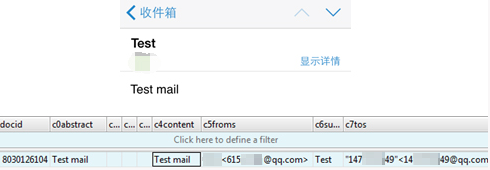
Finally, the example below shows an unencrypted messaging app's contact list. However, it is worth noting that the flaws in Whatsapp may no longer exist due to the recent implementation of end-to-end encryption.
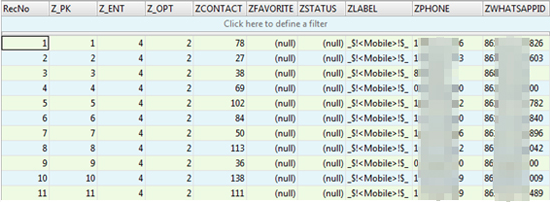
Interestingly, the lack of encryption in popular iOS apps cannot be said for Android counterparts. Trend Micro says that the databases for the Android versions of these apps are encrypted, which means cyberattackers would be required to decrypt any data they managed to steal. This may be due to the disproportionate rate of attacks against the Android operating system in relation to Apple's iOS platform. As there are relatively few iOS threats in comparison, developers may not have seen a need for additional encryption in iOS apps.
In order to protect yourself, your data and your devices from these kinds of security concerns, you should make sure your device is up to date and only download applications from trusted sources such as the App Store.
Read on: In the world of security