Hacking the Internet of Things
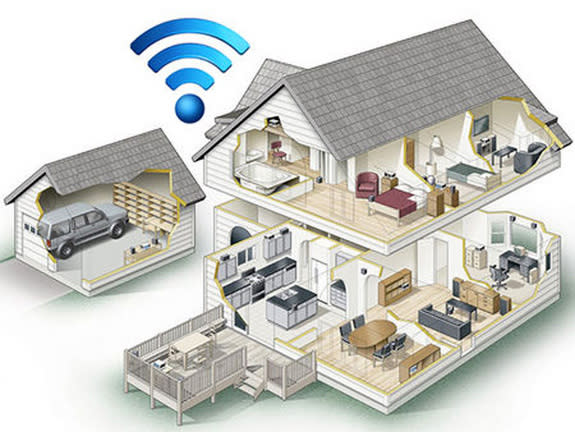
As the proliferation of smart devices begins in earnest, consumers may invite a whole new wave of security risks into their homes without even realizing it. Any device with an operating system can be hacked, be it a thermostat, TV or even a toilet.
In recent years, consumers have generally been wise enough to protect their computers from cybercriminals and harmful software. They've begun to protect their mobile devices in the same way, but their household electronics are woefully unprepared for the next wave of cyberattacks.
Smart household devices
There are all kinds of devices you can buy in order to convert your boring, ordinary old house into a "smart house." Using Wi-Fi-enabled devices, you can control your home's temperature, monitor your grounds, unlock your doors, control your lights and keep your food fresh.
MORE: 5 Free PC Security Programs Worth Downloading
Although it doesn't reveal as much information as hacking into a PC or a smartphone, malefactors can still compromise these devices, and in most cases, doing so is absolutely trivial. A hacker sending you a bogus grocery list might not sound like much of a threat, but someone unlocking your doors while you're out and helping themselves to your stuff could be a little more troublesome.
"Motion sensors, sirens, window and door sensors — those are marketed as secure devices with the assumption that … it would be very difficult for an attacker to [target them]," said Behrang Fouladi, a security researcher at SensePost. "This assumption is not correct."
At this year's Black Hat security conference in Las Vegas, the Internet of Things (nontraditional Web-enabled devices) was a hot topic. Multiple presentations suggested that security on these devices is, at present, almost nonexistent.
Fouladi and his colleague Sahand Ghanoun, an aerospace engineer, tested a number of smart devices controlled by ZigBee and Z-Wave communication protocols. Both ZigBee and Z-Wave are common wireless communication systems that communicate between devices via radio waves.
In addition, security researchers David Bryan, security consultant at Trustwave SpiderLabs; Daniel Crowley, managing consultant at Trustwave SpiderLabs; and Jennifer Savage, software engineer at Tabbedout, gave a presentation that examined a number of different smart devices and concluded that they were all more or less ripe for attacks.
Device breakdown
The Belkin WeMo switch was one of the most vulnerable products tested. The switch is fairly straightforward: Hook any electronic device up to it, switch it on or off via your smartphone, and do things like prime your air conditioner while you're finishing up yard work or brew your coffee while you snatch a few more minutes of shut-eye.
In addition to commandeering the device via its operating system, the researchers were able to monitor communications between the switch and the iPhone commanding it. This could be a mere annoyance if you're controlling a lamp in the bedroom or a real problem if you're controlling an electronic safe.
The Radio Thermostat faced similar problems: A complete lack of authentication means that anyone on the same Wi-Fi network with a working knowledge of its OS can adjust the temperature on a whim.
"Thermostats and lights are not very critical if they are compromised," Fouladi told Tom's Guide. "I don't care if someone, for instance, tries to turn off or turn on the lights … Something like a front-door lock or a motion sensor, if they are used to detect intrusion — that is critical stuff. The implication of the compromise is higher."
The biggest problems were present in the most sophisticated devices: the hubs. Both the MiCasaVerde VeraLite and INSTEON Hub centralize all of the smart devices in a house and allow a user to control them from one place. The Karotz Smart Rabbit consolidates your email, social networking information and music, and can broadcast it all to you by voice. It also looks like an adorable anime rabbit.
None of the three will keep you safe. The researchers compromised the VeraLite, but the company would not acknowledge the product's security flaws, much less fix them. The INSTEON Hub's OS lacks even basic authentication procedures.
Staying safe
For now, the safest route would be to avoid these devices altogether, but that might not be entirely sensible. Keep in mind that most of these vulnerabilities require an attacker to already be logged in to your Wi-Fi network. Unless someone is willing to hack into your Wi-Fi (which requires them to be nearby), this limits the potential offenders.
Many of these devices "cannot run heavy crypto algorithms or some complicated wireless communication protocol," Fouladi said. "The manufacturers need to consider a balance between the security and the actual-use case. If they want to build secure smart devices with the security coverage of a PC or an advanced mobile phone, that will be very expensive."
MORE: 5 Free PC Maintenance Programs Worth Downloading
There's also not much reason for malefactors to take an interest in most of these hacks. A really enterprising burglar might hack a WeMo switch that's hooked up to an electronic lock, but it's still easier to break a window. Fiddling with the temperature could ensure an empty house, but so would waiting until everyone's left.
The research at Black Hat is also all proof-of-concept work — there's no real evidence that hackers have attempted any of these stunts in the wild. Missing out on tech that could make your life more convenient on the off chance that someone could mildly annoy you with it is a shortsighted strategy.
Consumers can also be proactive before they purchase smart devices. "The customer can first check that the vendor is actually a certified Z-Wave or ZigBee producer," Fouladi said. "That would give him at least a good level of assurance that the device has passed lots of tests and has a reasonable level of security."
The rest, Fouladi said, is up to manufacturers. Rather than just assuming that Z-Wave or ZigBee functionality ensures security, they should employ security consultants to ensure that the systems are not vulnerable to simple attacks.
"These devices are not like software you can patch later," he said. "If they are shipped, it is very difficult to update those in the field."
Beyond that, watch out for that Karotz rabbit. It's got a vicious streak a mile wide.
This story was provided by Tom's Guide, a sister site to LiveScience. Follow Marshall Honorof @marshallhonorof. Follow us @tomsguide, on Facebook and on Google+. Originally published on Tom's Guide.
Copyright 2013 LiveScience, a TechMediaNetwork company. All rights reserved. This material may not be published, broadcast, rewritten or redistributed.


