When will individuals pay for security?
Last week's discovery of Lenovo bundling Superfish malware that chose to insert its own self-signing certificate authority into Windows' trusted certificate chain under the auspices of serving ads to Lenovo customers highlights the extent to which hardware makers will try to squeeze a profit out of a low-margin business.
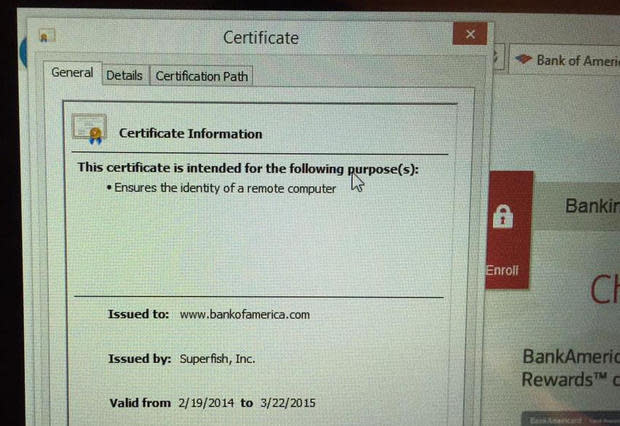
(Image: Screenshot by Chris Duckett/TechRepublic)
Throughout the Chinese hardware manufacturer's twisting and turning last week -- from outright denial of Superfish's security impacts to the weekend's mea culpa that Superfish was indeed a security concern and not the "potentially unwanted program" that Lenovo was trying to label it as -- perhaps the most damning admission was that the whole preloading affair was conducted late last year for a pittance.
"The relationship with Superfish is not financially significant; our goal was to enhance the experience for users," Lenovo's first statement on the issue said.
Sending its users' security down the river for a couple of pieces of silver is an issue that will deservedly stalk Lenovo and its reputation for some time. Ironically, during the middle of the crisis, Lenovo's chief technology officer Peter Hortensius told The Wall Street Journal that the company's reputation is how it survives.
"Our reputation is everything, and our products are ultimately how we have our reputation," he said.
At this point in the Superfish debacle, it is clear that whatever goodwill Lenovo had gathered over the years via its purchasing of business units from IBM is well and truly gone -- in knowledgeable circles, at least.
There's a very good reason why Lenovo chose to put Superfish onto its consumer line of laptops, and not on the highly prized ThinkPad line of devices: At some point, when considering the decision, it thought it could get away with it.
Presumably, the damage to its reputation that Lenovo would have had to cop if it began bundling software that installed its own root certificates into its enterprise line of machines was decided to be much greater than consumer devices. In the end, though, there doesn't seem to have been much difference once the extent of the security concerns were realised.
There has been an outpouring of sentiment against Lenovo, with many commenters swearing that Lenovo has seen the last of their money, and quite rightly so.
But will those thoughts translate into buying decisions and threaten the Chinese vendor's status as the number one PC maker in the world? While it is nice to consider Lenovo getting its comeuppance for its actions, the past has shown that little changes once these issues fall out of the spotlight.
After its rootkit fiasco, Sony still makes compact discs, and has done very well with its latest PlayStation; and despite efforts to boycott RSA over allegations that it took $10 million to use an NSA-backdoored algorithm as the default pseudorandom number generator for the company's encryptions products, RSA's 2014 revenue was up 5 percent.
If consumers truly wanted vendors to stop loading new machines with crapware and cutting corners to squeeze a meagre profit out of them, then they would have taken their dollars elsewhere a long time ago. The furore around Superfish does not only touch the Windows ecosystem; the same techniques are being used in the Android ecosystem, not only by hardware vendors, but by carriers, too.
For every informed buyer who would willingly pay extra to forgo the adware and "enhancers" that arrive on new PCs, there are a dozen more who would pay the lower price and remain blissfully unaware that their computing stack could be horribly compromised.
Given the overt choice between an adware-subsidised device, and a device with only a clean install of an operating system, one would hope that consumers choose the clean device in greater numbers. But Microsoft already does this with its Signature Edition devices and service, and Sony started offering the choice of a non-bloatware Windows installation called Fresh Start in 2008. In both instances, the option has been available for years, and yet the largest PC maker in the world still feels the need to go down the well-beaten preload path.
With knowledge of Superfish, though, an opportunity exists for a hardware maker to take advantage of the situation and offer a system free of bloat. Not only for performance reasons, but the ability also now exists to point to a catastrophic example of why preloading software for spare change is a terrible idea.
For consumers, too often issues that can be prefixed with cyber are filed away as being too complex to tackle, but as more and more of our lives are conducted online and make use of computing technology, cyber issues should just be issues.
At the end of this week, looking beyond the consequences that Lenovo will face, the question to be answered remains whether the industry and consumers will wake up to themselves and treat the issues around Superfish with the seriousness that they require, or whether, as usual, we will carry on as though nothing happened, and continue to take the cheapest option on offer, even if it happens to be a poisonous one.
If Superfish doesn't make us change our ways, it's hard to imagine an alternative situation that could.
