MacID iOS app: Securely access OS X with multi-factor authentication
In a recent article covering Sesame, a multi-factor authentication product, several readers responded with a request for more articles with a security focus. Sesame is just one great example of how a relatively small, lightweight product can enhance security beyond the traditional username/password combo. There are several other products on the market that provide a variation in enhancing the security of desktop access using hardware that many users will undoubtedly already possess: an iOS-based device.
Comparing one app to another would be akin to recommending a firewall over an IPS--both provide similar functions--however, they're implemented in different fashions and often seen as complimentary to each other. In this particular article, we'll take a closer look at the iOS app called MacID from Kane Cheshire.
MacID is an app for iOS/OS X that costs $3.99 (USD), and it functions as a replacement for the password combination used to access a modern Apple computer. Its strength lays in utilizing a piece of hardware as a trusted device that allows the end user to login to his/her computer by invoking the software on the iOS-based device and utilizing that trusted device plus the pin code, gestures, or fingerprint via Touch ID.
The iOS app works in conjunction with a parent app on OS X. Both devices communicate using Bluetooth 4.0's LE (Low Energy) standard, which in turn ensures that both end-points sip rather than gulp power while also encrypting bi-directional communication using AES-256. According to the developer's website, it never exposes information sent/received to the internet, which is a plus for users concerned with privacy.
Before reviewing the setup of MacID, let's first take a look at the requirements on both the OS X and iOS side of the app:
iOS: iPhone 4S or later, iPad (4th Gen or later), iPod Touch (5th Gen or later) running iOS 8+
OS X: MacBook Air 2011 or later, MacBook Pro 2012 or later, iMac 2012 or later, Mac Mini 2011 or later, Mac Pro 2013 or later running 10.10+ Yosemite
Bluetooth LE
Installation for both the iOS and OS X apps are pretty straightforward, yet configuration will require a few additional steps to customize it for your specific environment or to be in compliance with network security policies.
On the iOS device, install and then launch the app (Figure A)
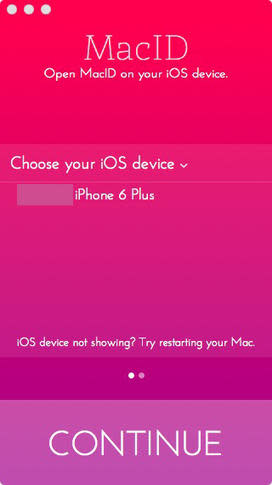
Figure AFigure A On the OS X device, copy the app to the Applications folder and launch it.
On OS X, the app will scan for iOS devices and list the names of the devices it finds. Select the desired device, and click the Continue button to proceed (Figure B).
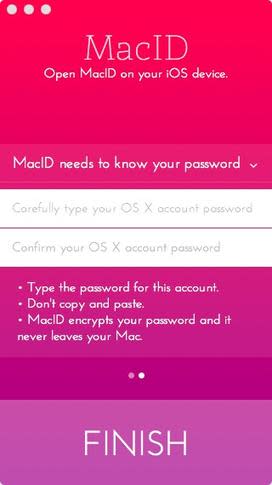
Figure BFigure B When prompted, enter the password to the user account on your Mac, enter it again to confirm the password, and click Finish to complete the trusted device configuration (Figure C).
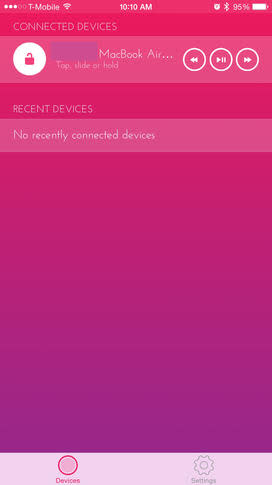
Figure CFigure C On iOS, the name of the OS X computer should now appear as a trusted device in the connected devices list. Both iOS and OS X have now been configured as trusted devices (Figure D).
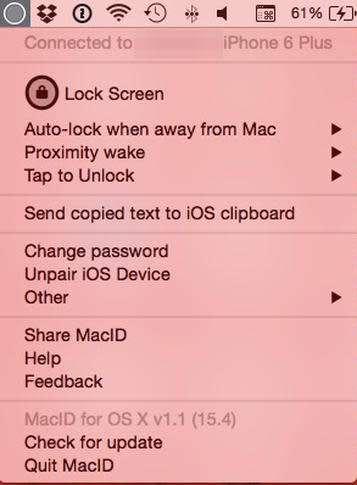
Figure DFigure D To lock down specific settings, access the MacID settings by clicking the icon in the menu bar. The trusted device (iOS) should appear on the top as a connected device. To test out the base settings, click Lock Screen from the drop-down menu. The computer will lock, and a prompt will appear on the iOS device that allows you to unlock the device by using Touch ID. If the device does not support Touch ID, then it will default to the pin code instead (Figure E).
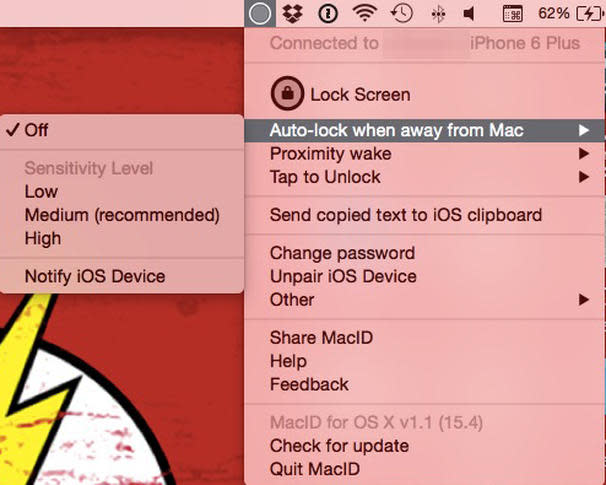
Figure EFigure E The first setting to configure is Auto-lock when away from Mac. This includes a section for setting the sensitivity and notification to the iOS device when the device becomes locked. Medium is the recommended level for most users. It also provides an auto-lock when the iOS device is moved approx. 35ft. away from the Mac (Figure F).
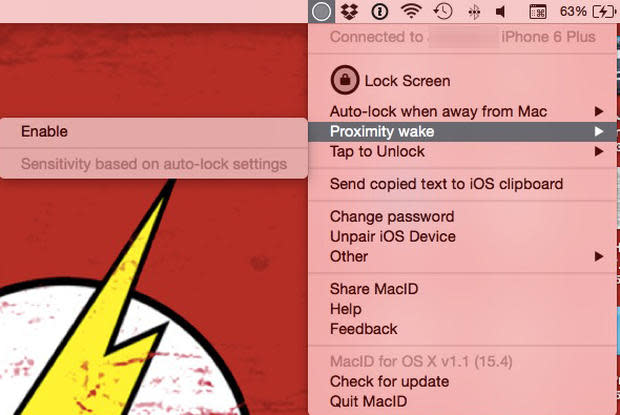
Figure FFigure F Next, Proximity wake allows the Mac to be unlocked when the device is back within range when enabled (Figure G).
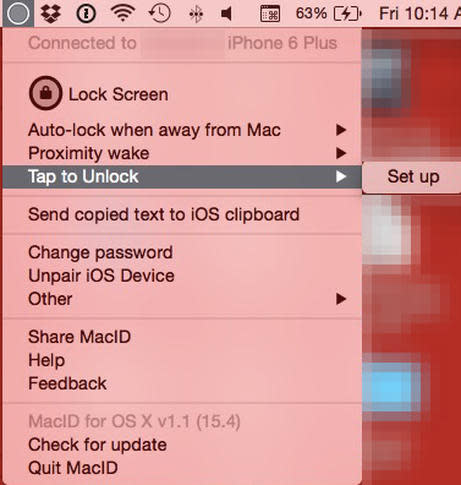
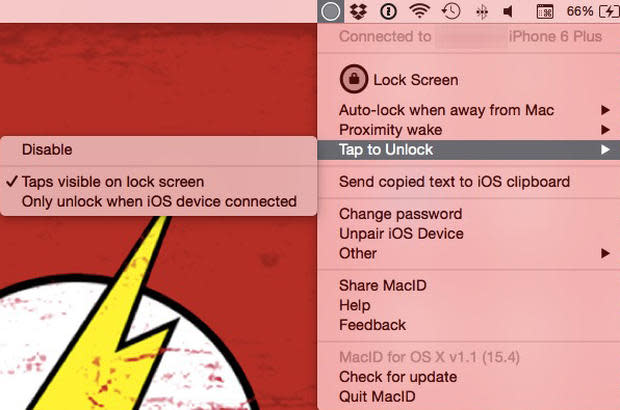
Figure GFigure G Tap to unlock is the next setting, which requires a bit more hands-on set up (Figure H).
Figure HFigure H
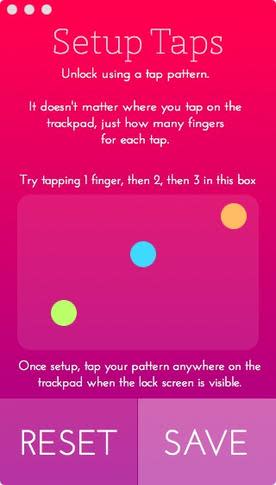
This feature is aimed at computers that have a trackpad, which when configured, will allow the end user to tap their fingers on the trackpad to create a gesture-like pattern to unlock their Mac (Figure I).
Figure IFigure I Once a pattern is created and saved to the app, selecting the Tap to unlock setting again will yield two other settings: Taps visible on lock screen and Only unlock when iOS device is connected. These two settings extend security further by enabling a true, multi-factor authentication experience and should not be overlooked (Figure J).
Figure JFigure J Once the OS X settings have been configured to your satisfaction, it's recommended to test out the settings by locking and unlocking the Mac with your iOS device and testing out the notifications as well (Figure K).
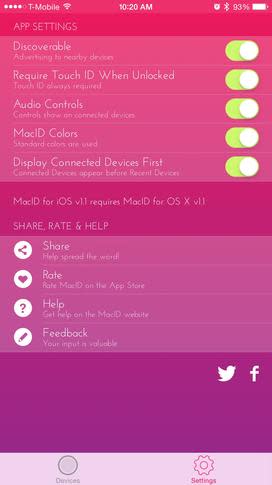
Figure KFigure K Lastly, tapping on the Settings button on the iOS app will reveal a few settings that may be tweaked to further enhance the usability of the MacID (Figure L).
Figure LFigure L
In real-world testing, I found MacID to be a solid performer, not missing a beat in the locking or unlocking phase. As with any app though, there are a few key points--both good and not--that were encountered that may (or may not) be a deal breaker for utilization in the enterprise.
The good
The app has incredible accuracy, easily handling locks/unlocks with ease each time
Lightweight, easy to use for all users, regardless of skill level
Low battery consumption, thanks to Bluetooth LE
AES-256 data encryption in both directions
Privacy is secured as neither app communicates via internet
Low price point for app implementation per device
Password may still be used as a backup in the event that the iOS device is lost, stolen, or powers off
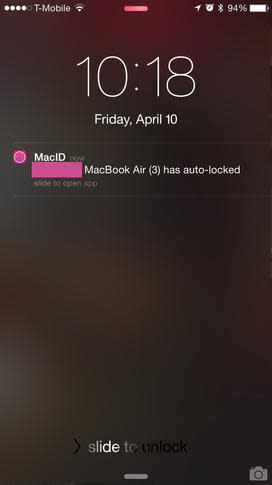
Notifications for iOS inform end users when their Mac has been locked and unlocked
Needs work
Sensitivity levels, even on low, still require iOS device to be moved 20+ ft. from Mac to auto-lock (not ideal for smaller offices/businesses)
Not a true multi-factor authentication solution by default, as it serves more as a replacement for having to manually enter a password instead of performing a secondary check prior to allowing access
Enterprise rollout could prove difficult without the ability to configure settings remotely or via .mobileconfig XML file
Requires modern Mac computer and iOS device to implement/use (older devices using a prior Bluetooth spec are not supported)
Awesome feature(s)
Touch ID stores encrypted OS X password in secure enclave so the password is never exposed, even if the iOS device is lost or stolen
Setting up Tap to unlock enables two-factor authentication when gesture and only unlock when iOS device is connected are used
Use of MacID allows for end users to set a password utilizing a greater key space, since the user would not be required to remember it, instead defaulting to using the iOS device to handle locking/unlocking (this greatly enhances security and will likely curb shoulder surfing or brute force methods of password retrieval)
What tools do you use to securely connect iOS to OS X? Share your experience in the discussion thread below.