Two-month wait for government POODLE patch
On October 14, the Google Security Team revealed a serious flaw in Secure Sockets Layer version 3.0 (SSLv3), advising the removal of SSLv3 fallback support.
However, as recently as December 11 -- almost two months after Google's announcement -- Australia's Department of Health was found to still be using the 18-year-old protocol on its Therapeutic Goods Administration eBusiness Services (eBS) website.
The affected page was updated to use the newer Transport Layer Security (TLS) protocol this week, after ZDNet made contact with the government department, alerting representatives of the vulnerability.
A spokesperson for the TGA told ZDNet in an email that it knew about the vulnerability and had been working since November -- a full month after Google's disclosure -- to apply a fix to its site.
"The TGA was aware of the 'Poodle' vulnerability, and has been working since mid November to address the issue," a TGA spokesperson said.
"A fix has been applied to the TGA eBS website production environment.
"The patch to address the vulnerability was tested in the TGA training environment."
At the time of writing, the TGA had not responded to ZDNet's query as to why it waited for almost a month from Google's initial announcement before working to address the issue.
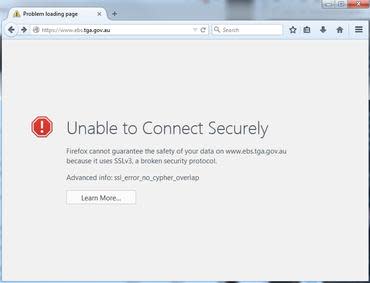
Having already disabled SSLv3, Firefox 34 would not load the vulnerable site prior to its update. (Image: Screenshot by Leon Spencer/ZDNet)
The flaw, dubbed Padding Oracle On Downgraded Legacy Encryption (POODLE), allowed an attacker to conduct a man-in-the-middle attack in order to steal "secure" HTTP cookies or other bearer tokens such as HTTP Authorisation header contents.
While SSLv3 has long been made obsolete by TLS, the potential impact of POODLE was large, due to handshaking procedures that occur when setting up a secure connection between HTTP servers and clients to establish a common protocol to communicate.
In October, Google outlined steps to take in order to protect against the vulnerability:
"Disabling SSL 3.0 support or CBC-mode ciphers with SSL 3.0 is sufficient to mitigate this issue, but presents significant compatibility problems, even today. Therefore, our recommended response is to support TLS_FALLBACK_SCSV."
The search giant also included a fix in its Chrome 39 release aimed at preventing the SSLv3 fallback, and the Chrome 40 release will see the removal of SSLv3 support entirely. Firefox removed SSLv3 support from its browser with the release of Firefox 34 on November 25.

