Edward Snowden: The complicated man behind an epic heist
Listen : Apple Podcasts | Google Podcasts
In June of 2013, Edward Snowden was working a contractor job as a systems administrator for the National Security Agency (NSA). During that time, he allegedly stole 1.5 million classified files.
He then flew to Hong Kong where he met with journalists, providing them with documents which detailed abuses by both the NSA and its partners. These journalists published story after story with this information, and sent shock waves through the world.
A few days later, Snowden identified himself as the American whistleblower, and caught a flight to Moscow two weeks later — where he lives to this day.
The Art Of The Exit by Yahoo Finance is a true crime podcast that goes inside some of the most notorious heists in history. Listen here, and subscribe for a new episode coming next week.

This story has countless layers of complexity. Was Snowden protecting the privacy rights of his fellow citizens? Or did he have ulterior motives behind the curtain? Both? What kind of person was Snowden before the leaks, and what will this end up costing the United States when it is all said and done? We discuss it all in this episode of The Art Of The Exit.
“I think he’s a very complicated figure,” Yahoo Finance editor and Snowden expert Michael B. Kelley explained. “He was obviously very disgruntled. There was a certain anger in his actions.”
“It seems, from an observational point of view, that he stole information unrelated to civil liberties or the things that would make him a whistleblower, so he goes beyond that,” Kelley added. “The question becomes: How far did he go? I don’t think that has been answered yet.”
When looking into his past, one can find clear patterns. He struggled within systems and pushed back against authority. Snowden had an antagonistic online personality, along with power struggles with superiors at work. In his new book, he avoids certain topics about his life and exile.
To hear the full story, listen to The Art Of The Exit.

Full transcript of the episode below:
TV Commentator :(00:00) Edward Snowden, hero or villain?
TV Commentator 2 : Well, it's possible to be a bit of both.
Alex Sugg: (00:09) In June of 2013, Edward Snowden was working a contracted job as a systems administrator for the NSA. In his time there, he allegedly stole 1.5 million classified files from the NSA. He then flew to Hong Kong, where he met with journalists, and provided documents which detailed abuses by both the NSA and its partners. These journalists took that information, and published story after story, which sent shock waves through the internet and the world. A few days later, Snowden identified himself as an American whistleblower, and caught a flight to Moscow a few weeks later, where he lives to this day. This story has countless layers of complexity. Was he a hero or a traitor? Was Snowden protecting the privacy rights of his fellow citizens, or did he have ulterior motives behind the curtain? What kind of person was Snowden before the leaks, and what will this end up costing the United States when it's all said and done? This is the story of Edward Snowden, the man behind the biggest information heist in history. You were early on the scene with Edward Snowden, so maybe tell me what was going on with you. You were writing about the whole situation, you also uncovered a lot as it was starting to progress. So maybe just tell your story.
Michael B. Kelley: (01:51) Yeah, the Snowden leaks came at a great time for me professionally and personally, in the sense that, as a young reporter at Business Insider, I was interested in national security, and I was interested in specifically domestic spying. So when Snowden came out, it really hit directly on my beat.
AS: (02:12) This is Michael B. Kelley, my colleague at Yahoo Finance. He's an expert on the Snowden case, and agreed to help tell the story.
MBK: (02:19) And so I covered it immediately. And then something interesting happened. The leak started on June 5th, 2013, and he identified himself on June 9th Hong Kong time. Then two days later, after he identifies himself, Edward Snowden, American whistleblower, he gives an interview with the South China Morning Post. He also provides documents to that reporter, Lana Lam. And those documents were actually detailed operations against China as opposed to domestic surveillance activities of the NSA, which was the big kind of reveal of the Snowden documents. When he gave that interview saying, "I have more documents, I have to go through them all, I did not provide these documents to the journalist before," and the actual details of the documents were foreign intelligence operations of the US against China, it piqued my interest in a different way.
MBK: (03:20) And when I asked an expert, a cyber expert who had worked with NATO to put together the international rule book called the Tallinn Manual for cyber operations, he said, "Yeah, what Edward Snowden revealed to the South China Morning Post is just spying. It's just a an updated version of espionage that's been going on forever, but now the technology is much better." At that point, my mind kind of went on parallel tracks where it was obvious that the early Snowden leaks had exposed something that was important for American society, and started a privacy discussion that continues to this day. There was also this aspect of, well, why is he also leaking this information that doesn't really have that same public interest in mind, and it really is only helpful to the people he's leaking it about, namely the Chinese government.

The Art Of The Exit by Yahoo Finance is a true crime podcast that goes inside the most notorious heists in history. Listen here, and subscribe for a new episode coming next week.
MBK: (04:18) And even Glenn Greenwald, who was the main and most aggressive journalist on the Snowden case, and one of the three journalists that Snowden really worked with and provided documents to, he was asked by a reporter at the time, and he said, "Yeah," basically paraphrasing that if he had to guess, it would be that Snowden was trying to ingratiate himself to the people of Hong Kong and the authorities. And that in itself is a recognition that Snowden was no longer acting out of altruism. That was a very selfish act in the sense that he was trying to save himself from being caught by authorities or handed over to the US. And so that added an extra element to the whole story.
AS: (05:02) So was everybody else seeing this divergence? Like you said, these two parallel tracks, trains of thought almost of like he's a good guy on one side, and a bad guy on the other side? Or was that unique to something you noticed then that maybe others hadn't?
MBK: (05:17) There weren't that many people who noticed it. If you speak to former government officials at the time, they certainly noticed it. They knew the difference between those two pieces of information. William Binney, who was a mathematician at the NSA for 30 years, he ended up quitting right after 9/11 because he believed that there were abuses being committed. He actually came out after Snowden leaked that information to the South China Morning Post and said, "Well, he's transitioning from a whistleblower to a traitor," which is a pretty wild statement. And a couple years later, I actually asked Bill Binney about that statement, and he said when pressed, he said that he stood by that statement. And Binney's kind of a hero to Snowden, so that's a fascinating aspect. But for the most part in 2013, those leaks, the initial ones really just rocked everyone, and they kept coming. There was a really good story developing, which was Edward Snowden, the whistleblower, the champion of privacy and everyone's freedoms. That was really the dominant story, and so this subtext that there was this other element to it didn't really catch on at the time.
AS: (06:28) That subtext Michael is referring to has become the most interesting part of the story to me. When looking at motives, it always just comes down to the person. Who was Edward Snowden before he began handing over those documents? Was he a brave patriot willing to put his whole life on the line to create more transparency in the US, or is there something else behind these actions? The only way to get any clear direction is to look at Snowden's life before the leaks. Why don't you tell me what you know about him? What made Edward Snowden the way he is?
MBK: (07:06) Yeah, that's a really fascinating part of the story, and it's a different part of the story, but it's part of the story that becomes important when evaluating intent. Why does anyone do anything? And we are the end of all the actions that we've taken before now, and we are created by the context in which we grew up.
MBK: (07:33) Edward Snowden, born in 1983, so depending on where you put the cutoff of millennial, he's right there. He's one of the original digital natives. He liked computers. He was very good at it. He took to it very well. He grew up in North Carolina, for a time, lived not far from Fort Meade, where the NSA is based. He grew up in a government family. His mother works for the courts. His father worked in the Coast Guard. He had a tough teen years. He dropped out of high school when he was about 15, and he says it was because he got mono, and just didn't go back. His parents got divorced when he was 17 going on 18, and he was basically at that point on socializing mostly on the internet, on these Ars Technica forums.
MBK: (08:23) So the first time he logged on was December of 2001. Over the next 10-plus years he is on and off. But on those forums, his last post is right before he allegedly started stealing documents. You learn a lot about his personality. He calls himself an indoor cat now when he lives in Moscow, because he's just on his computer all the time.

The Art Of The Exit by Yahoo Finance is a true crime podcast that goes inside the most notorious heists in history. Listen here, and subscribe for a new episode coming next week.
AS: (08:43) Gotcha. You said one thing that I want to kind of dig at. He dropped out of high school because he claimed to have mono, you say that saying like we, a lot of people get mono, and it doesn't take them out of high school necessarily. What do you think was the real story there? Like what, what caused that you think?
MBK: (09:03) It's impossible to say based on what we're going on in terms of, these online artifacts of his posts online. He rails against institutional schooling. He doesn't like the system. He never liked the system. Whatever system he's in. And the first time we see that is through this school system. So, yeah, it's true that almost everyone knows people who had mono in high school, and those people didn't drop out. So it suggests that there was a larger context there. And it becomes interesting for Edward Snowden's life, because a lot of times medical reasons become important at different stages. So he joined the Special Forces training program, and this is right around when the Iraq War is really heating up, and he basically washed out, but he says that he broke both of his legs in a training accident. So there's another medical reason for him to leave this institution, this different institution, and people haven't, his medical records haven't been published because that's a privacy thing.
MBK: (10:13) But the official reason for him leaving was an administrative discharge, wasn't a medical discharge. And if you talk to former officials, that's kind of a big difference. And even if he would have broken his legs, if he wanted to stay in the program, he could have, just like if you get mono in high school, and you want to stay in high school, there are ways that they can accommodate, even in the military. And most famously, when he left the NSA in Hawaii to go to Hong Kong with all this documents, he told his boss that he had to go to a doctor because he had epilepsy. So there's another medical reason to leave an institution, but that was actually just his cover story so that he could get a few good days time, lead time.
MBK: (11:03) Just his cover story so he'd get a few good days lead time to go to Hong Kong.
AS: (11:04) Yeah. This is something that's repeated itself, a pattern in his story. We spoke a little beforehand and you said something interesting that I wanted to talk about too, because clearly he was online, like you said, an indoor cat, even back then, but he also had interests in gaming, right? Wasn't that part, like he was an arcade visitor?
MBK: (11:26) Yeah, he talks about the arcade in Maryland. He was really big into Tekken. On one of the internet pages that he was on he put his occupation as Tekken and he's on all these different threads, but over the years he's consistently on video game threads, whether it's arcades, talks a lot about tech and he talks About Dance Dance Revolution, which is another arcade game, but he's also on console games about Metal Gear Solid 2. He's definitely a gamer of the times.
AS: (12:03) Right. His presence online, was that generally positive? Was it just talking to friends, talking about gaming? Were there other sides to the story other than just being a teenager, young kid talking to your buddies about video games online?
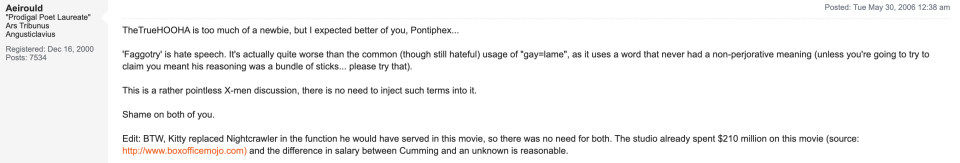
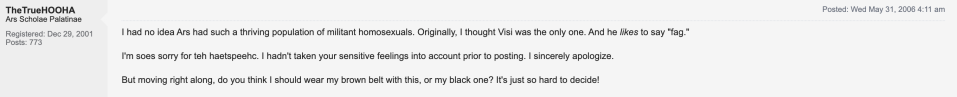
MBK: (12:18) Yeah, that's an interesting question, particularly in this day and age when you have people, celebrities, where what they've said in public before is basically being mined and brought back up and used against them in certain ways, and with Snowden, yeah, there's an element of, he's a young guy and there's obviously a bit of anger in him and so he's just kind of throwing words around as a lot of young men do, but he also stands out within this community of mostly men as being pretty aggressive. It's up to each individual person to chalk it up either as a young guys, just boys will be boys kind of thing, but that kind of response doesn't resonate as much as it did even a few years ago. So there are some fascinating examples of him being in discussion and responding to someone's argument as faggotry and another user will push back and say, "You know, faggotry is hate speech. This is a pointless conversation about X-Men. You don't need to be bringing in these terms," and Snowden would just double down and saying, "Oh, I had no idea ours had such a thriving population of militant homosexuals." So really playing that up and at the time he's 23 years old, so it makes me think that when I was 23 years old, was I speaking like that? No, I wasn't online like that either, but it makes it interesting that he kind of has this history himself of words he used that we can evaluate within the context of the time.
The Art Of The Exit by Yahoo Finance is a true crime podcast that goes inside the most notorious heists in history. Listen here, and subscribe for a new episode coming next week.
AS: (14:18) Maybe walk me through what's going on with him while he's in his contract, the one where he's actually beginning to gather information, maybe right before he actually starts stealing it or when he says he starts stealing?
MBK: (14:31) At one point he said, I think it was to NBC, he said that when he washed out of the army special forces program, he had to find another way to serve. He got a job at a facility on the campus of University of Maryland as a security guard and it was actually a language school, so it's technically a DOD facility. He's basically an SA security guard, working the night shift for a few months, and he had to go through the security clearance process, then he worked as the security guard for five months or so. When he left that job, he took with him a very valuable thing, which is a security clearance. Once he had his security clearance, he's basically known to the system.
MBK: (15:19) He applied reportedly at a job fair. He applied to the CIA and got picked up despite not having traditional schooling.
AS: (15:32) Right. I was going to say he dropped out of high school...
MBK: (15:32) Dropped out of high school.
AS: (15:34) It's pretty wild that he was able to land such a great job with...
MBK: (15:38) Yeah and you know, it depends who you ask. Some formal officials say that he had to have some fault pull, like ask his grandfather who was a Rear Admiral, who had worked on joint task force with CIA and FBI, and was connected or Mike [Morale 00:00:15:54], the former Acting Director of the CIA, and his book says that post 9/11 the CIA needed telecommunications analysts. They needed people and it's clear that Snowden definitely knew computers and definitely knew this stuff, so wherever you fall on that spectrum, he got hired by the CIA.
MBK: (16:14) Basically throughout his time at the CIA we know from interviews with his superiors that were publishing a declassified assessment in December, 2016, he was basically clashing with superiors from the beginning of his training program. He thought that he knew better than his superiors in certain ways and he had this habit of CCing people much higher on the food chain.
AS: (16:43) Okay.
MBK: (16:44) And this is another trend of Edward Snowden, like the medical thing. He did this several times in his time in the CIA and the NSA where...
AS: (16:53) So he was bringing in the boss's boss's boss kind of thing?
MBK: (16:56) Yeah. At one point he, according to this assessment, he CC'd someone who is the head of the CIA Directorate overseeing what he was doing and that person was one of a couple dozen highest CIA officials, and he was a trainee, but he thought that the situation wasn't being handled well so he was going to CC someone who he thought could handle it.
MBK: (17:17) A memo written in September of 2008 whereas Snowden's CIA superior described him as an energetic officer with a plethora of experience on Microsoft operating systems. Also "Often does not positively respond to advice from senior officers, does not recognize the chain of command, often demonstrates a lack of maturity and does not appear to be embracing the CIA culture."
AS: (17:42) Snowden's life has clear patterns. He struggled within systems and pushed back against authority. As Michael mentioned, Snowden's antagonistic online personality, along with his struggles with superiors at work., give a snapshot into what he was like.
AS: (17:59) Now is that proof that he is a villain without a heart? No, but it is proof that he could be a very difficult man to be around and that he had problems living within a system the he didn't control.

AS: (18:13) After the break, we go through the details of how Snowden was stealing information and what this case ended up costing the United States. Snowden is said to have stolen around 1.5 million classified files from the NSA before fleeing to Hong Kong. I asked Michael how exactly was he able to do it without being noticed.
Alex Sugg: (18:45) I want to know how Snowden was doing this. I picture he's headed to the office. He has pockets full of hard drives and he's just plugging them into computers left and right and just stealing and stuff. I know that's silly and probably an unrealistic idea of what was going on. Can you tell me how, practically, he was taking these files and these documents?
Michael B Kelley: (19:09) Yeah. It definitely wasn't as presented in the Oliver Stone film where he just had one thumb drive and he stuck it in for a few minutes and then put it in a Rubik's cube and walked out.
AS: (19:23) Uh-huh (affirmative).
Michael Kelly: (19:24) This was pretty systematic. The way that it was described to me by people with knowledge of the matter, was that he was clever.
The Art Of The Exit by Yahoo Finance is a true crime podcast that goes inside the most notorious heists in history. Listen here, and subscribe for a new episode coming next week.
MBK: (19:36) People use the word hack, but he really used a few workarounds and he was smart about what workarounds he had and the access that he had for him to devise a system that worked for him. The best we know about this is from the House Permanent Select Committee on Intelligence. They released their report in late 2016, basically a review of the disclosures.
MBK: (19:59) They say here that he used several methods to gather the information. As they do with the tone of this document, they add "None of which required advanced computer skills." I think that's kind of an unnecessary jab. I think this was pretty smart. People who are experts said that this was clever. I'm sure it didn't require full state level style hacking as we would think of it, but this was pretty clever.
MBK: (20:27) What he did was... Part of his job was to collect files and move them and one of the basic things he'd do was just a scraping tool that allowed him to collect a bunch of files, which was he was able to do through his system administrator privileges, and start pulling files. That is an easy way to do it because it's passive collecting of those things unless...
MBK: (20:52) The other thing that he was able to use his system administrator privileges for is access to personal network drives, apparently. He could copy what was on colleagues drives, because that was part of his job, and there are people who had admitted to providing him with a password. In the course of his duties he could use that password, but he could also use them for nefarious purposes to get more data and copy anything of interest.
MBK: (21:18) One fascinating anecdote in here is at some point in 2012, a fellow system administrator noticed that his personal drive used significantly larger amount of memory than most other employees and asked him what he was doing Stone responded that he was downloading system patches for NSA network, a task that was consistent with his job responsibilities and then the next line is redacted.
MBK: (21:37) So he was able to kind of use his day to day job to mask the fact that he was actually moonlighting and stealing these files.
AS: (21:47) Right. So just to clarify that last point, someone saw him with a much fuller drive than normal and asked him about it and he had a quick cover up, essentially?
MBK: (21:57) Yeah. Yeah, he was able to brush it off and really the most interesting thing in this report...
MBK: (22:03) Really, the most interesting thing in this report that it explains is they allege, and this is mostly from an NSA security official, which is what makes this document so interesting, as a system administrator, he did a lot of stuff on the backend and he devised a system where he was actually had access to another machine. He would basically go return to his old desk after hours allegedly to do some of this downloading. It was about a 20 minute drive away, and so he's driving back and forth at night to his old desk, and what they allege in this document is that he had ... his new job didn't require him to visit that old building.
MBK: (22:50) So this was another thing that he said, "Well, I can still get into the old building and that's the machine I need to pull the stuff out," so he was just using that. The long and short of it is is that he took advantage of his systems administrator access, he took advantage of whatever access he got when he moved over to Booz Allen, and he, when at Booz Allen he used his old thin on thick machine, took advantage of this loophole that allowed him to go back at night and secretly steal these documents, and he, according to the HPSCI report, he removed an estimated 1.5 million documents from the secure systems.

AS: (23:42) You said to me and where you're first discussing the story, this could be considered the most notorious intelligence heist of all time, and especially the fact that he essentially has gotten away scot free for the most part. But I know that there is a financial implication. I'm know that there are many. Will you talk about those as well? Maybe what this has cost the United States estimated. What are the costs involved in what happened with Edward Snowden?
MBK: (24:09) Yeah, there are a few different costs in terms of ... there's the cost of the resources spent by the NSA and the FBI in terms of trying to track them down and work this case. The NSA, we know from the black budget that Snowden leaked and was published in the Washington Post, that their budget is about $10 billion a year and they were moving resources around to do that, so there's the costs of that. There was the cost of reputational damage to US companies after this because it was basically people started thinking that the US government could tap into your Facebook, that was like the simple person, the simple explanation that people would understand if they weren't really following the news, but they'd heard about it, they thought that the US government could get into all these companies, which was not the case.
MBK: (24:57) It was nowhere close, but these big tech companies do have a law enforcement relationship, so they took reputational damage. There was a great paper in February of 2017. It was updated by Microsoft research office and they kind of looked at all the existing estimates of how much money was lost, and they said that the expected losses to the US cloud industry were at least $18 billion. That's one kind of quantitative figure on it. This paper makes a really fascinating point in that for these individual companies, they had to spend money to harden encryption. They had to win the trust back of their customers, and so they spent some money kind of investing to create more solid structures, and that's arguably a good thing. Apple leading the way in terms of encrypted phones, but it was forced to ... Edward Snowden forced the hand, and then current day and looking now there's the fascinating aspect of Huawei. Huawei being a Chinese telecom companies that the US alleges is very close to the Chinese government, and they're the world's leading telecom equipment provider. The worry is, is that they could access other countries systems simply by having back doors in their telecom equipment.
MBK: (26:14) The US is fighting a very high-stakes, diplomatic kind of battle right now, banning Huawei from the US and trying to lobby allied governments and not use this, and one of Huawei's defenses against US accusations is, "Oh, well, just look at what Edward Snowden showed us. The US government is the one doing this. We're not doing this." So he's kind of used as a shield to deflect this kind of criticism, which is fascinating. You can't really quantify that, but it does have an effect on commerce today, which is kind of one of the interesting long tail effects of Snowden.
AS: (26:59) Last question, and this is your opinion that I'm asking. Is Edward Snowden a hero or a villain?
Michael Kelly: (27:11) So sometimes I think about a story that I wrote covering this in the summer 2013, and the headline is Edward Snowden is both a patriot and a traitor. I think that that story has aged pretty well. The basic thesis of it was that he's a patriot for exposing, providing evidence of post-911 domestic surveillance activity. That moved the ball forward in terms of the conversation of post-911 abuses, and there's that transparency argument that it's really ... there's a commendable part of that and the reforms that have come out after that.
MBK: (27:56) Then there's this other shoe about all the rest of the stuff, and I'm really ambivalent because I think that both of those things can be true. I think he's a very complicated figure and I'm interested in the ... that's why I spent time looking into the person because he was obviously very disgruntled again and again in his life and there was a certain anger in his actions, and it seems from just an observational point of view that he stole information unrelated to civil liberties or the things that would make him a whistle blower, and so that he kind of goes beyond that. The question becomes how far beyond did he go, and that's an interesting question and I don't think it's been answered yet.
The Art Of The Exit by Yahoo Finance is a true crime podcast that goes inside the most notorious heists in history. Listen here, and subscribe for a new episode coming next week.
MBK: (28:52) We could do one of these episodes just on the colorful words used by The True HOOHA, Snowden's alias on the ARS Technica forums between the years 2001 and 2012, and one of my favorites is from June 12th, 2008. This would be right before Edward Snowden turned 25. He's working for the CIA at the time, and he writes his own, he starts a forum post and it's titled, Okay, okay. This is getting real. I had a vision." The post reads, "I woke up this morning with a new name. I had a vision. A dream vision. A vision righteous and true. Before me I saw gamers. Gamers shrouded in the glory of their true names. Step forth and assume your name in the Pantheon. It's always been there. Your avatar's true name. It slips through your subconscious, reveals itself under your posts, and flashed visibly in that moment of unrestrained spite in the indulgent teabag. You felt it, known it, recognize it. Now realize it. I woke up this morning with a new name. That name is Wolfking. Wolfking Awesomefox."
MBK: (30:23) This is ... it's just a really fun and interesting post that captures a lot of Edward Snowden's personality, and even if you break down the etymology of this name, Wolfking Awesomefox, it has this kind of voraciousness to it. It has this kind of illusions of grandeur to it, and that's exactly who his personality was online. People say that Edward Snowden is related to The True HOOHA. That would be his alias, but really Edward Snowden's true alias is Wolfking Awesomefox.
AS: (31:15) How far beyond did Snowden go? Only time will tell exactly, but one thing is certain. Edward Snowden committed the most notorious intelligence heist and history, and he got away unscathed. He's living in Moscow now and will be for the foreseeable future. As he said himself, he's an indoor cat, so I wouldn't expect to see him outside anytime soon.
AS: (31:50) The Art of the Exit is produced by Yahoo Finance at our studios in New York City. This episode was written, edited, and produced by me, Alex Sugg. Thank you to Michael B. Kelley for your time and walking us through all the details of the Snowden story. If you enjoyed this episode, please head over to Apple podcasts and leave us a five star rating and review there and share the story with your friends. We'll be back soon with another new episode, so until then, thank you for listening to The Art of the Exit.
Listen : Apple Podcasts | Google Podcasts
Follow Yahoo Finance on Twitter, Facebook, Instagram, Flipboard, SmartNews, LinkedIn, YouTube, and reddit.

