How do keys open locks?

Curious Kids is a series for children of all ages. If you have a question you’d like an expert to answer, send it to curiouskidsus@theconversation.com.
How are keys made, and how do they open locks? – Noli, age 12, Wisconsin
Have you ever wondered how keys work? I teach a course in computer security where we learn how locks function – and also how they can be broken or bypassed. We do this because locks teach important principles about security in general.
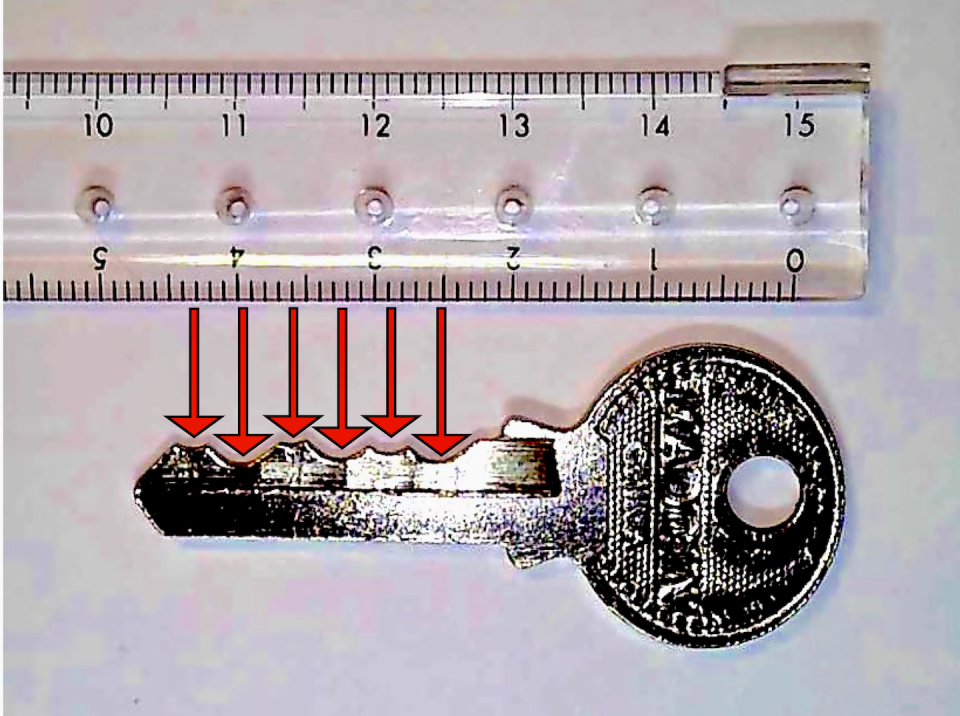
If you look closely at a key, you’ll see its top edge has a bunch of V-shaped valleys. If you inspect the key more closely, perhaps with a ruler, you’ll notice the bottoms of these valleys are equally spaced. The depth of the valleys encodes a sequence that is accepted by the lock, with each valley contributing one value to the combination.
Inside the lock is a cylinder – the part that moves when you stick your key in and turn it. The key can turn only if all its valleys are the right depth for your particular lock.
But how does your lock detect whether your key’s valleys have the right sequence of depths?
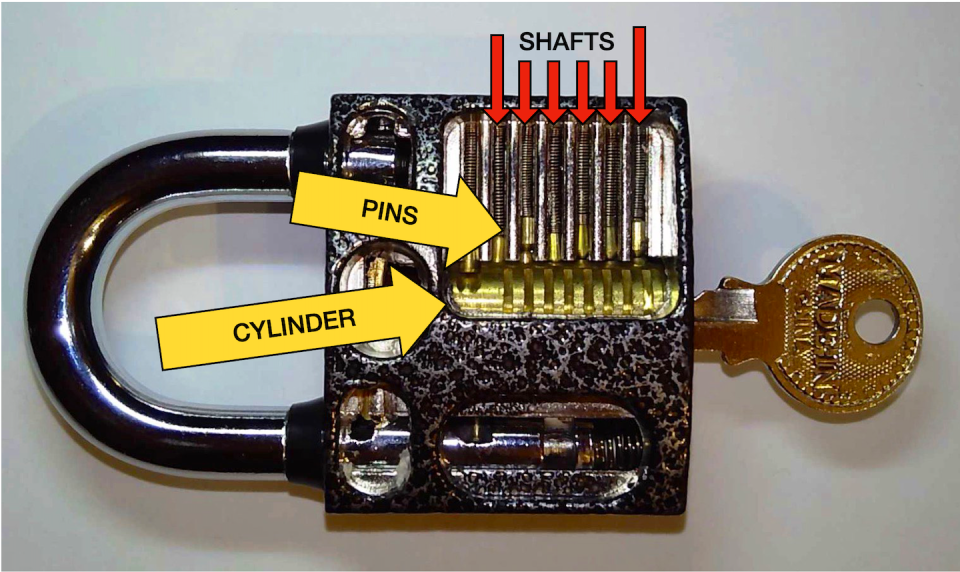
Inside the lock are vertical shafts, one over each valley of the key. In each shaft is a pair of metal pins that can freely slide up and down. Depending on where the pins are, they can block the cylinder from turning and prevent the lock from opening. This happens whenever a pin is partially sticking into or out of the cylinder.

When you stick a key in the lock, the pins fall into the valleys. If a valley is too high, it causes a pin to stick out and jam the cylinder. If a valley is too low, the pin sinks too low and the pin above it will sink into the cylinder and jam it. However, if the right key is inserted with the valleys at just the right depths, none of the pins get in the way.
Keys are made by placing a blank key into a grinding machine that is programmed to carve out the exact valleys that are needed. A locksmith can also change a lock by removing its pins and fitting it with new ones to match a chosen key.
In computer security, we say that security relies on “something you know, something you have or something you are.” A password is an example of something you know. A key is an example of something you have. A fingerprint would be an example of something you are. But as you can see, a key is also very much like a password, except it is encoded by grinding a piece of metal.
For this reason, you shouldn’t ever post a picture of your house key on the internet. That would be like posting a picture of a credit card or a password – someone could use the photo to duplicate the key.
It is also possible to unlock or “pick” locks without a key. By sliding a thin piece of metal into the cylinder and gently pushing the pins to the correct height one by one, locks can be opened. However, it takes a great deal of skill and practice to do this.
What does this teach us about security? First, we must make keys secret by making a very large number of possible keys, so that the right one is hard to guess or build. It’s the same for passwords. Second, it’s important to engineer a lock or computer program that requires every bit of the key or password to be exactly correct.
It’s important to study the inner workings of locks and computer programs to understand how their design might allow someone to break them.
Hello, curious kids! Do you have a question you’d like an expert to answer? Ask an adult to send your question to CuriousKidsUS@theconversation.com. Please tell us your name, age and the city where you live.
And since curiosity has no age limit – adults, let us know what you’re wondering, too. We won’t be able to answer every question, but we will do our best.
This article is republished from The Conversation, a nonprofit news site dedicated to sharing ideas from academic experts. If you found it interesting, you could subscribe to our weekly newsletter.
Read more:
Scott Craver does not work for, consult, own shares in or receive funding from any company or organization that would benefit from this article, and has disclosed no relevant affiliations beyond their academic appointment.
