Why Firefox Is Moving to DNS Over HTTPS—and What That Means for You

If you use Firefox, you'll see a change to your browser's security encryption starting today.
According to a blog post from Mozilla, Firefox's parent company, the browser will be moving to DNS over HTTPS (DoH) standard.
What's that? It's a fancy term that basically increases user privacy and security by preventing man-in-the-middle attacks.
Let's say you're an engineer and you want to send a confidential set of graphics to your attorney, complete with specs for a new patent application you want to file soon. So your lawyer emails you back: "Just click this link to my firm's page and upload it there," she writes. "That's easiest for me."
Fair enough. You trust her, so you send over the goods. There's just one problem: That website might have looked legitimate, but it was actually a fake. You've been tricked into forking over valuable intellectual property to a total stranger in what's known as a man-in-the-middle attack. Whoops.
To prevent these kinds of hoodwinks, Firefox—Mozilla's web browser and a popular alternative to Google Chrome—has announced a new security protocol to avoid such shams. It's called "DNS over HTTPS," also known as DoH, and it's a way to ensure that data traveling between your computer and a company's server is encrypted, keeping middleman hackers out of the equation. DNS stands for Domain Name System and HTTPS stands for Hypertext Transfer Protocol Secure.
This cybersecurity approach is being embraced by other browsers and websites, too, just not necessarily by default. You can enable DoH in Chrome, for instance, and even Facebook supports a move to more secure DNS.
{% verbatim %}
DNS, HTTPS, DoH, it's a lot of acronyms.
The most important thing to know is we're basically saying FU to attackers on the network and 3rd parties who have access to data that ties your computer to the sites you visit.https://t.co/S6GpzuMEJR— Firefox 🔥 (@firefox) February 25, 2020
{% endverbatim %}
The DoH rollout will be a default setting only in the U.S. If you live in another country, you can enable the security protocol by going to Settings > General > Networking Settings > and clicking the Settings button on the right. Enable DNS over HTTPS by ticking the checkbox next to that prompt.
First, Let's Talk About HTTP

Mozilla Hacks, a blog that the company's Developer Relations team publishes, has put together a useful series of cartoons that offer a clear-cut explanation of what's going on here.
Let's start with HTTP, the internet browser protocol that you usually see at the start of a domain name, like http://gmail.com. These links are now shortened to, in this example, mail.google.com, but if you type in "http://" before the site name, you'll still find the same page.
When a browser downloads a web page, it makes what's called a GET request, which basically retrieves information from the server. Then, the server sends a response, containing an HTML file. This whole process is referred to as HTTP, which stands for hypertext transfer protocol, since it's all about sending information back and forth.
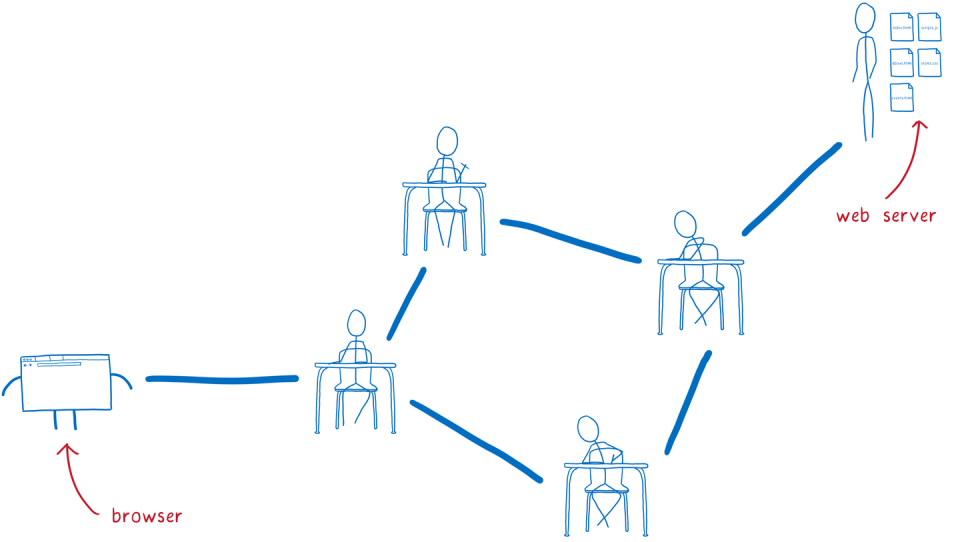
But your computer probably isn't all that close to Google's servers in that Gmail example. Instead, the request needs to get from the browser to that server, passing through multiple channels before it gets there. Mozilla Hacks likens it to passing notes in school:
I think of this like kids passing notes to each other in class. On the outside, the note will say who it’s supposed to go to. The kid who wrote the note will pass it to their neighbor. Then that next kid passes it to one of their neighbors — probably not the eventual recipient, but someone who’s in that direction.
But this method opens a can of worms. Anyone along the server's path can basically read the contents. Worse yet, there's really no way to know which path your information will flow through to get to that main server. It could end up in the hands of bad actors, looking to perpetrate man-in-the middle attacks.
Why DNS Is Vulnerable

Domain Name Systems are what allow us to easily type web addresses like wikipedia.com without having to memorize a long string of numbers that technically house a site's IP address. The process of converting the number string to an intelligible IP address that's simple to remember is called domain name resolution. The issue? Some of the resolvers helping you to connect to a website are controlled by cybercriminals.
During the resolution process, your IP address or other information about your identity is accessed to help you find the domain you're looking for. That means every sever along the path to helping you reach the website sees the sites you're looking to find. "But more than that, it also means that anyone on the path to those servers sees your requests, too," according to Mozilla Hacks.
That puts your data at risk in two main ways: tracking and spoofing.
Tracking
Bad actors can create a record of all of the web sites they’ve seen you look up. That's valuable data, because companies will pay big money to see what you're searching.
Spoofing
A hacker along the path between you and the DNS server can actually change the response. Instead of telling you the real IP address for Wikipedia, for instance, a spoofer will give you the wrong IP address for a site, according to Mozilla Hacks. "This way, they can block you from visiting the real site or send you to a scam one."
Here's an example from Mozilla Hacks:
...Let’s say you’re shopping for something at Megastore. You want to do a price check to see if you can get it cheaper at a competing online store, big-box.com.
But if you’re on Megastore WiFi, you’re probably using their resolver. That resolver could hijack the request to big-box.com and lie to you, saying that the site is unavailable.
Man-in-the-Middle Attacks
Here's where it all comes together.
This is your classic middleman scenario, except nobody is trying to sell you anything—just striving to intercede your communications. Three players are involved: the victim, the entity the victim wants to communicate with, and the so-called middle man, who interprets all of the victim's communications. Meanwhile, the victim has no idea their communications are being surveilled.
Here's how it goes down, according to NortonLifeLock, a cybersecurity software services firm in Mountain View, California. First, let's assume you've received an email from what appears to be your bank, asking you to log in to confirm your contact information. Seems innocuous, enough, right? So you click the link in the email and you're taken to a page that really does look like your bank's website. You log in and perform the action that your "bank" requested.
Meanwhile, according to Norton, that email was generated by a man-in-the-middle perpetrator, who wanted to make the message look legitimate. Yes, this involves some rudimentary phishing—getting people to click on fraudulent links—but this trickery takes things a step further. The bad actor went through the trouble of creating a website that mirrors your real bank's home page, to keep from rousing any suspicion. So in the end, you're not giving that sensitive contact information to your bank—you're giving it to a man-in-the-middle hacker who just duped you.
How to Protect Yourself
Even if you don't use Firefox, you can take several precautions within any web browser to protect yourself from man-in-the-middle attacks. Here's some advice, per Norton:
• Make sure "HTTPS"—with the S—is always in the URL bar of the websites you visit.
• Look out for potential phishing emails from attackers asking you to update your password or any other login credentials. Instead of clicking on the link provided in the email, manually type the website address into your browser.
• Never connect to public WiFi routers directly, if possible. A VPN encrypts your internet connection on public hotspots to protect the private data you send and receive while using public WiFi, like passwords or credit card information.
• Since man-in-the-middle attacks primarily use malware for execution, you should install a comprehensive internet security solution on your computer. Always keep the security software up to date.
• Make sure your home WiFi network is secure. Update all of the default usernames and passwords on your home router and all connected devices to strong, unique passwords.
You Might Also Like
